Public Key Infrastructure
Solution for identification, confidentiality and other security issues are possible by application of digital signature and cryptography methods. In this sence, Public Key Infrastructure (PKI) is one of the significant elements in the area of information Technologies.
PKI settles many tasks by use of asymmetric cryptographic algorithms according to public key technology. Identification of people, protection of data integrity, determination of data source issues are solvable on information environment.

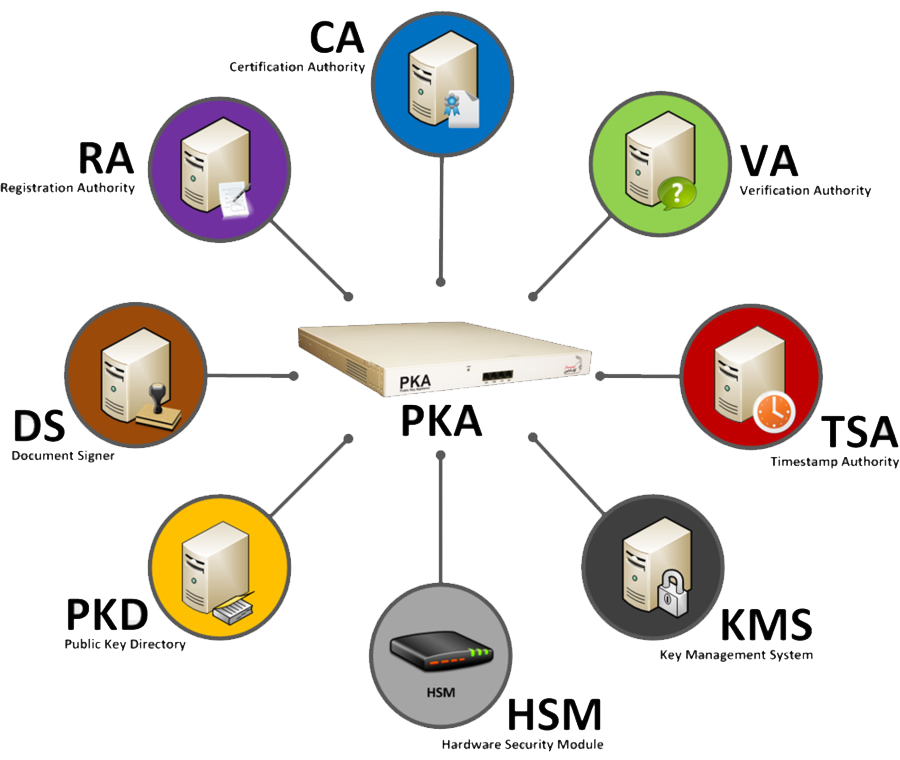
The main leading element of PKI is a Certification Authority (CA) hierarchical chain of trust. CA - as a trusted source, carries out of people identification by using of digital certificates and assymetric keys.
The process of secure exchange of keys among people on PKI technology based on asymetric cryptographic algorithm is provided and this ensures data integrity and safely delivery by encryption.
Digital Certificate
As a guarantor of establishment of digital certificates providing identification on keys, their control and as well as other security princiles, CA fully provides security on electronic environment. Settled by digital certificates, digital signature is deemed to be equal to hand signature and sets issues as protection of data integrity and source determination. Pursuant to performing cryptography of data by asymmetric keys, loss of data is impossible in any case.
Main features of the system:
- Creation and management of more than one certification center in one server;
- Creation of public/private key and submission of digital certificate request by web enrollment service of certification centre;
- Full integration with HSM for the purpose of security of CA keys;
- User keys can be generated and stored in smartcards and eTokens;
- The secure management service for registration authority;
- Registration of all transactions log;
- System is developed on the base of international standards and local legislation for digital signature;
- Time Stamp Authority(TSA) service;
- Software for generation of digital signature and library for cryptographic methods;
- Technical functionalities for accreditation with government Root CA;
- Support of different range of cryptographic algorithms (RSA, DSA, SHA1, SHA2, ECDSA);
- Online Certificate Status Protocol (OCSP) service;
- Mobile application for creation of digital signature and encryption data;
